Remote Install Keylogger Through Email
To do this, you will have to consult your PC's documentation, as each PC handles this process a little differently. Secret: If your system does not boot from the DVD, you may need to change the system's boot order so that the optical drive is checked before the first hard drive. Windows vista accessories missing. Some systems, however, do not provide this warning and will instead boot from the DVD by default.
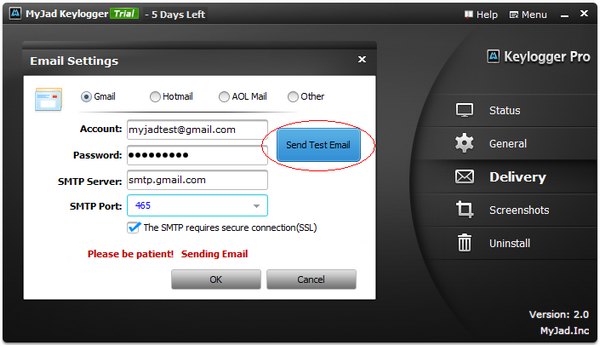
- In this article we will look at the best remote keylogger for a PC, Android, and iPhone. How To Send a Key logger Through Email or Text Message This is one of the most common questions we get over here at pcTattletale.
- Mostly, there are two kinds of remote keylogger: 1. Remotely installable keylogger. You can embed the keylogger into an email, word file or something else. The target will be infected once the user clicks and opens the file with keylogger. This kind of keylogger is a sort of virus or Trojan horse.
Free Iphone Keylogger Remote Install
I think my partner is cheating but I do not have access to his computer and it would be weird to ask to use his when I'm over (we don't live together). So I'm wondering what is the best Keylogger with Remote Installation? And how do these work? I've done a bit of research but still a noob. Obviously there would be a file they need to open to activate, say I send via email? And how do you get it past anti virus/protection software? It would be great if there is a free option, but I'm willing to pay for quality. Thanks for your help! (I realise there are other threads based around this but would like an up to date option)
Free Remote Install Keylogger
Create a special installation link for your chosen remote keylogger Send a link to a target person via email or private chat It should not be too suspicious, so a target person could click on it. There are many resources available for assistance in doing this available on DuckDuckGo. Download the Keylogger. Install the Keylogger Software. Set the password for the encrypted file. Set up the program. Name your Keylogger. Enter the 15 digit code that has been sent to your Email. Right Click on the Keylogger icon and select options. Also, it is possible to use keylogger on the work, to control the performance of employees. And finally, keylogger is a perfect backup tool for text information. Use keylogger every day on your computer, and you will never lose your passwords, logins and other critical information. In fact, this stealth keylogger can be installed remotely using a pre-configured package and then continue doing its job autonomously, while the admin will receive its results via email, network or uploads to an FTP server.